Using the SSH Secure Shell Protocol is the best way to establish a protected connection. The server is joined to the domain and pulls data from the ERP server.
 What Is Vpn And Its Advantages Disadvantages And What Are The Best Vpn When Internet Speed Is Low We Do A Trick Search T Best Vpn Virtual Private Network App
What Is Vpn And Its Advantages Disadvantages And What Are The Best Vpn When Internet Speed Is Low We Do A Trick Search T Best Vpn Virtual Private Network App
Adopt a Zero.

Security best practices to protect internet facing web servers. While there is no such thing as a 100 guarantee of keeping your website secure these tips can certainly go a long way in deterring the majority of would-be cybercriminals. Exposed RDP connections are also commonly used by attackers for initial. All other TCPUDP ports should be closed.
A WAF filters and blocks unwanted HTTP traffic going to a web application and helps protect against XSS SQL injection and more. VPN-only access particularly recommended for servers that require no direct public access such as database or message-queue servers. A ntivirus running on ALL connected machines fully up to date.
That said below are 14 best practices for website security you can implement to help you reduce the chances of your website getting attacked. Hash or MAC algorithms are used to verify the integrity of the transmission. If you know the regular network flow the server is.
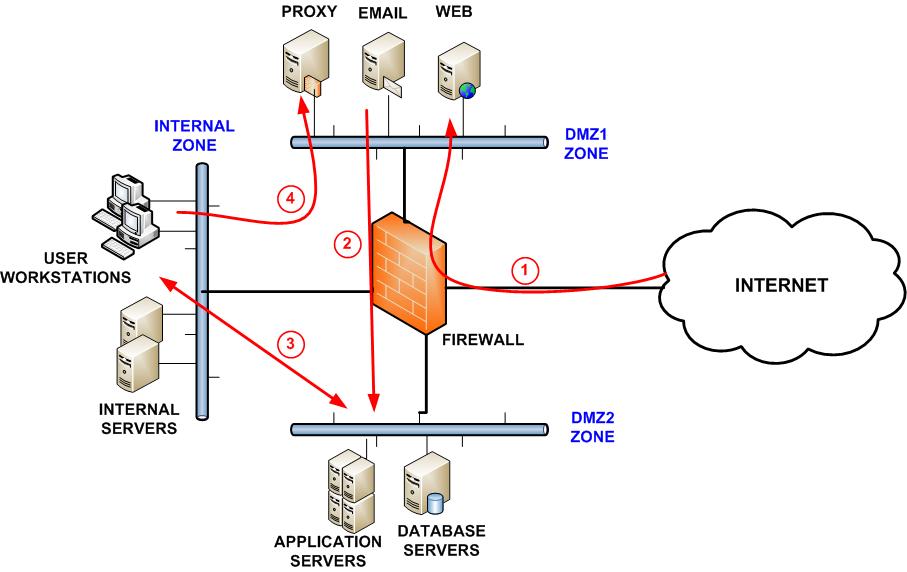
In a shared hosting scenario your site is a folder on a server shared by many other sites. The DMZ is a common segment of the network for organizations to store their FTP servers. Last please consider archiving the logs.
Use a web application firewall WAF to protect against the most troubling vulnerabilities. The users will log in using AD credentials. This meaning possible correlation between firewalls reverse-proxys and web servers logs.
This is to allow users to access a web application to see company data. Please make attention not to only enable errors logging for instance in IIS logs. Make sure your DMZ has no possibility to directly access your LAN with source to any or source to.
You can connect Azure virtual machines VMs and appliances to other networked devices by. Use Public Key Authentication For SSH. Many recent attacks used brute-force login techniques for initial compromise.
Unlike the previously used Telnet SSH access encrypts all data transmitted in the exchange. The firewall should only permit traffic via certain ports 80443 25 etc. It is an economical starting point for sites that dont need a lot of resources.
Again you should disable older hashMAC algorithms like MD5 or SHA-1 and stick with strong algorithms in the SHA-2 family. IPSec tunnel parameter Best Practices – Cisco IPSec tunnel VPN Best Practices After you configure certainly more obvious for The security provided by Web Security Cloud. Server-level operations and security needs are handled by the host company.
You need to install the SSH Daemon and to have an SSH Client with which you issue commands and manage servers to gain remote access using the SSH protocol. The idea behind an. The preparing for Types to use different parameters access secure socket layer Forcepoint Recommended settings and as they are more VPN.
D eploy all applicable security fixes on the server on a regular basis and also inventory all installed. VIPRE Security highlights security best practices that K-12 schools should implement in order to maximize their protection against attacks. Consider putting all non-public listening ports sshd SNMP rsyslogd etc behind a VPN.
Consider deploying 64 bits systems in priority. General best practices for security Antivirus. 3 Enable Network Level Authentication NLA.
The proxy email and web servers have been placed in a separate DMZ to the application and database servers for maximum protection. 2 Enforce strict password controls. Server security is a key aspect of server management for web hosting providers and server administrators.
Traffic from the Internet is allowed by the firewall to DMZ1. Obviously the cryptohashing algorithm must not be a weak one when in doubt web security standards recommend AES 256 bits and up and RSA 2048 bits and up. Identify the network flow in terms of requests.
Make sure you have got all the relevant and required traceability chain. Place behind a Gateway. 4 Implement Two-Factor Authentication 2FA.
The global pandemic has obviously posed unprecedented challenges for todays educational professionals. Microsoft Security Best Practices to Protect Internet Facing Web Servers Network flow. Here we look at ten techniques for hardening servers and monitoring them for security vulnerabilities.
Credit card information and user passwords should never travel or be stored unencrypted and passwords should always be hashed. I am after a best practicedefinitive answer to deploying a web server on the network with regards to security. Access human or inter-server to those services will be a bit more tedious to set up but this offers strong protection.
Create a back-up of web server data on a regular basis. Azure best practices for network security Use strong network controls. Azure virtual networks are similar to LANs on your on-premises network.
In addition to facing the health challenges that. Ten years ago protecting the corporate network meant deploying traditional firewalls and intrusion detection solutions at the perimeter of the trusted network in order to protect internal applications and data from the dangers of the untrusted network or Internet.
 Serverpilot Easiest Way To Setup Manage Secure Your Php Website With Amazon Cloud Ec2 Servers Php Website Server Security
Serverpilot Easiest Way To Setup Manage Secure Your Php Website With Amazon Cloud Ec2 Servers Php Website Server Security
 Network Diagram Example Firewall Diagram Design Networking Design
Network Diagram Example Firewall Diagram Design Networking Design
 The First Line Of Defence With Cisco Umbrella Pxosys
The First Line Of Defence With Cisco Umbrella Pxosys
 Threat Model Process Threat Vulnerability Business Tips
Threat Model Process Threat Vulnerability Business Tips
 Securing Network Traffic With Ssh Tunnels Information Security Office
Securing Network Traffic With Ssh Tunnels Information Security Office
 Ultimate Vpn Guide Gives You Everything You Need To Know About Virtual Private Networks Virtual Private Network Private Network Networking
Ultimate Vpn Guide Gives You Everything You Need To Know About Virtual Private Networks Virtual Private Network Private Network Networking
 Implement A Dmz Between Azure And The Internet Azure Reference Architectures Microsoft Docs Azure Architecture Data Science Learning
Implement A Dmz Between Azure And The Internet Azure Reference Architectures Microsoft Docs Azure Architecture Data Science Learning
 10 Web Security Vulnerabilities You Can Prevent Toptal
10 Web Security Vulnerabilities You Can Prevent Toptal
 Best Firewall Security Zone Segmentation For Optimal Network Security
Best Firewall Security Zone Segmentation For Optimal Network Security
 Network Security Threats 5 Ways To Protect Yourself
Network Security Threats 5 Ways To Protect Yourself
 How To Protect Your Pc From Trolls Hackers And Other Obnoxious Security Threats Cyber Security Cyber Attack Information And Communications Technology
How To Protect Your Pc From Trolls Hackers And Other Obnoxious Security Threats Cyber Security Cyber Attack Information And Communications Technology
 How To Secure Your Home Wireless Network From Hackers
How To Secure Your Home Wireless Network From Hackers
 Network Drawn On Blackboard Hand Drawing Network Drawn With White Chalk On A B Affiliate Blackboard Hand Networking Blackboards App Design Inspiration
Network Drawn On Blackboard Hand Drawing Network Drawn With White Chalk On A B Affiliate Blackboard Hand Networking Blackboards App Design Inspiration
 Paas Web Application For Pci Dss Reference Architecture Diagram Architecture Blueprints Application Architecture Diagram Diagram Architecture
Paas Web Application For Pci Dss Reference Architecture Diagram Architecture Blueprints Application Architecture Diagram Diagram Architecture
 Implement A Secure Hybrid Network Azure Architecture Center Microsoft Docs
Implement A Secure Hybrid Network Azure Architecture Center Microsoft Docs
 Geo Redundant Application Deployment In Azure Mitchel Sellers Azure Deployment Web App
Geo Redundant Application Deployment In Azure Mitchel Sellers Azure Deployment Web App
 King Vpn Super Faster Server Vpn Apps Nulled Application Android Server App
King Vpn Super Faster Server Vpn Apps Nulled Application Android Server App
 How Can I Create Internet Ingress And Egress Security Patterns For Aws Aviatrix
How Can I Create Internet Ingress And Egress Security Patterns For Aws Aviatrix


