Best Php Obfuscator V.199 Free Unlock Code
Overview
Understanding the take a chance
When an application is beingness created, the Compiler will compile the application source code into several object files made of car linguistic communication code. Then the object files are linked together to create the terminal executable.
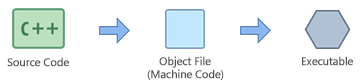
Effigy 1: Compilation of your source code
In the same manner that the source lawmaking of an application is converted into machine code at compilation time, at that place are tools that tin convert a compiled application into assembly language or a higher programming language. These tools are known as dissemblers and de-compilers.
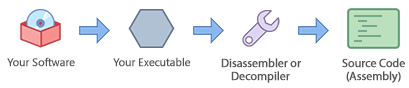
Figure 2: Decompilation of your application
An assaulter can employ a dissembler or de-compiler to study how a specific application works and what a specific routine does. When the attacker has a skillful knowledge of the target application, he tin alter the compiled application to modify his behavior. For example, the attacker could bypass the routine that checks for the trial flow in an awarding and make it run forever or even worse, cause the application to behave equally if it was registered.
Software Protectors
Software protectors were created to keep an attacker from directly inspecting or modifying a compiled application. A software protector is similar a shield that keeps an application encrypted and protected against possible attacks. When a protected application is going to be run by the operating system, the software protector will offset take control of the CPU and bank check for possible cracking tools (dissemblers or de-compilers) that may be running on the system. If everything is condom the software protector will keep to decrypting the protected awarding and giving it the control of the CPU to exist executed as normal.
The advantages of using a Software Protector are:
- Protect an awarding against piracy.
- Prevents attackers from studying how an application is implemented.
- Will not permit attackers to alter an application to change its behavior
The Weakness
Since software protectors were born, many attackers take centered most of their efforts on attacking the software protectors themselves instead of the applications. Many tools accept been developed that aid in the attacking of software protectors. These attacks often result in the attacker obtaining the original awarding that is decrypted and has the protection wrapper removed.
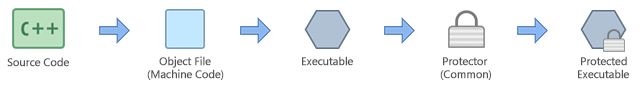
Figure three: Common software protectors philosophy
The chief problem with software protectors is that they use protection techniques very well known by crackers, and so they can be easily bypassed with traditional bang-up tools. Another of import problem in software protectors is that they have restricted execution by the operating system, that is, they run with normal application privileges. Considering of this attackers can use cracking tools that run at the same priority level as the operating system assuasive them to fully supervise what a software protector is doing at a certain time and attack it in specific places.
Revolutionary Solution
With Themida® , nosotros have centered in the main weakness that software protectors take thus providing a complete solution to overcome those bug. Themida® uses the SecureEngine® protection engineering that, when running in the highest priority level, implements never seen before protection techniques to protect applications confronting advanced software cracking.
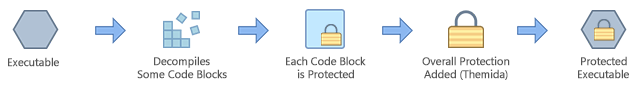
Figure 4: Themida® protection process
SecureEngine® defeats all current bang-up tools that tin be used confronting protected applications and information technology will make sure that your protected applications are only run in condom environments.

Effigy 5: SecureEngine® technology adds more force to the existing protection
Current Protectors Claim to be the Best!
Software protection programming is not a very well known field for nearly programmers. Software protection techniques are not like “visible” features that can be seen and compared. Because of this well-nigh software protection authors could talk about impressive techniques that are included deep within the protection scheme, when many times almost of these techniques hardly exist or they are much simpler than what they seem. Most software protectors reiterate a lot about using very strong cryptographic algorithms like RSA, Elliptic curves and AES hoping that the final user will believe that those protectors and the ambiguous algorithms are unbreakable. This if far from the truth every bit software protection is very different from data protection. Fifty-fifty if a software protector encrypts the protected application with the most robust cryptographic algorithm, sooner or later the protected application needs to be decrypted in order to be run past the CPU. It is in this phase when near attackers will commencement their work by dumping the decrypted awarding from memory to disk thus not having to deal with the cryptographic algorithm and reconstructing of the original awarding.
The Mission
In Themida® we want to be realistic about which weakness can be exploiting by attackers and what we really need to pay attending to protect an awarding with the highest security possible against software cracking.
Features
These are the cardinal features of Themida®:
- Anti-debugger techniques that find/fool any kind of debugger
- Anti-memory dumpers techniques for any Ring3 and Ring0 dumpers
- Dissimilar encryption algorithms and keys in each protected application
- Anti-API scanners techniques that avoids reconstruction of original import table
- Automatic decompilation and scrambling techniques in target awarding
- Virtual Machine emulation in specific blocks of code
- Avant-garde Mutator engine
- SDK communication with protection layer
- Anti-disassembly techniques for whatever static and interactive disassembler
- Multiple polymorphic layers with more than 50.000 permutations
- Avant-garde API-Wrapping techniques
- Anti-monitors techniques confronting file and registry monitors
- Random garbage lawmaking insertion between existent instructions
- Specialized protection threads
- Advanced Threads network communication
- Anti-Memory patching and CRC techniques in target application
- Metamorphic engine to scramble original instructions
- Advanced Entry indicate protection
- Dynamic encryption in target awarding
- Anti-tracing code insertion between real instructions
- Advanced Anti-breakpoint director
- Real fourth dimension protection in target application
- Compression of target application, resource and protection lawmaking
- Anti-“debugger hiders” techniques
- Full mutation in protection code to avoid pattern recognition
- Real-fourth dimension simulation in target application
- Intelligent protection code insertion inside target application
- Random internal data relocation
- Possibility to customize dialogs in protected application
- Back up of command line
- Many many more…
Screenshots
-
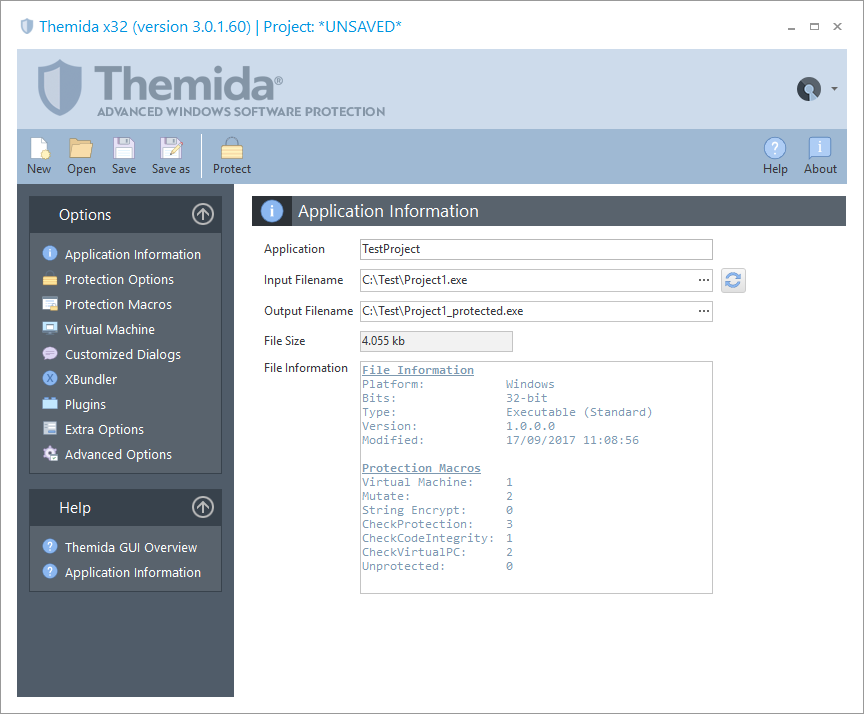

Application Info
Allows you to select the file that is going to exist protected. Also, it shows specific information about the selected file
-
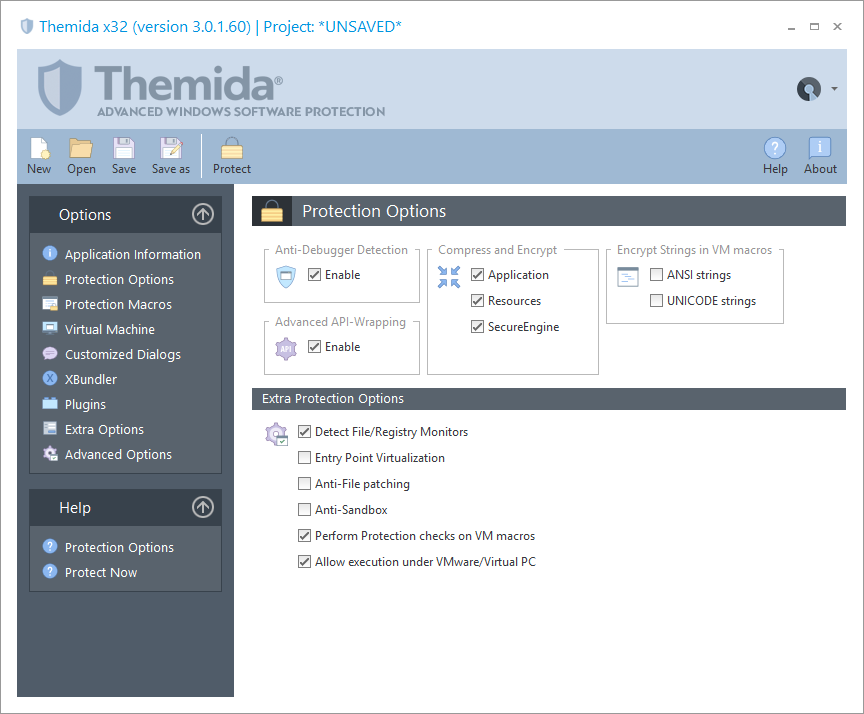

Protection Options
You tin can select the dissimilar protection techniques that will be added in your application.
-
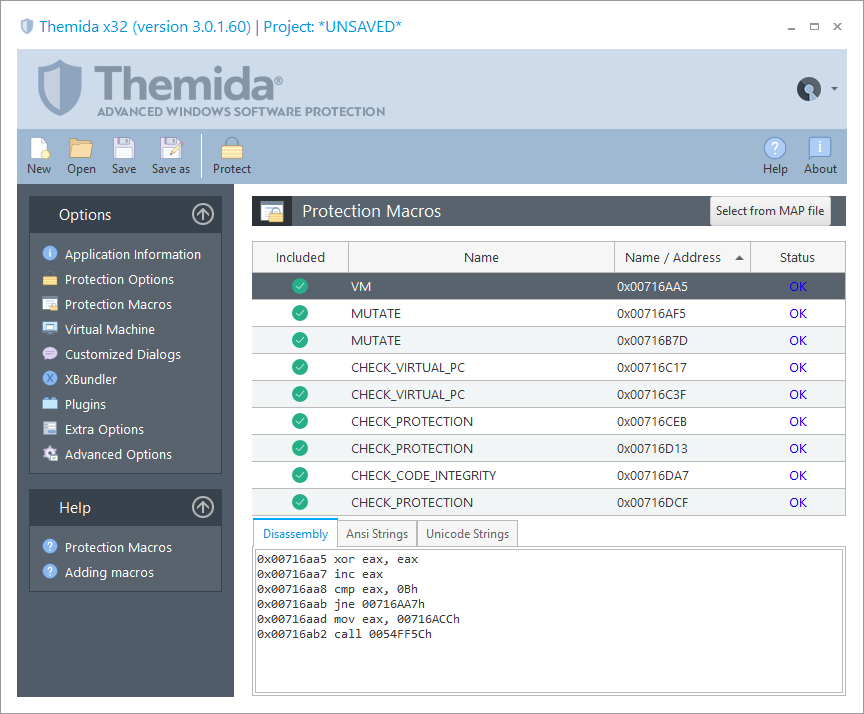

Protection Macros
The Protection Macros panel allows you lot to cheque all your macros inserted.
-
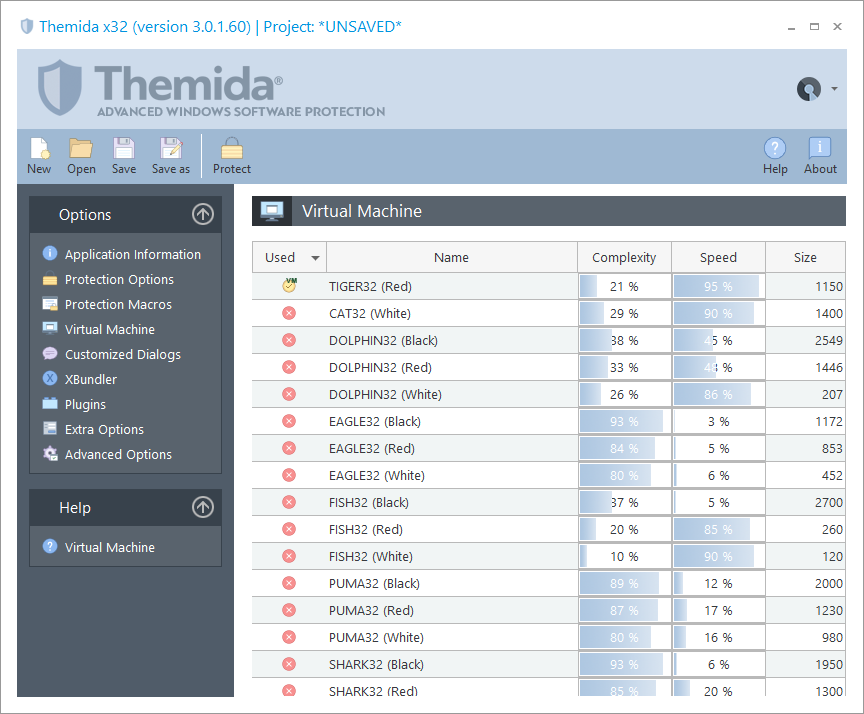

Virtual Machine
The Virtual Machine panel allows yous to integrate the Virtual Machine technology into your application.
-
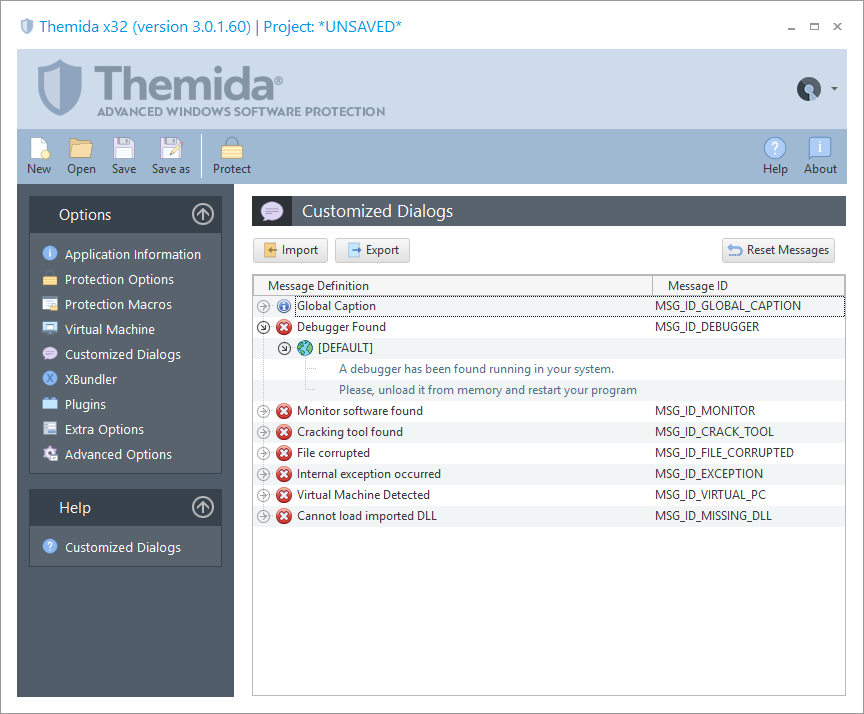

Customized Dialogs
Allows you to customize the unlike error or warning messages that could be shown in a protected application.
-
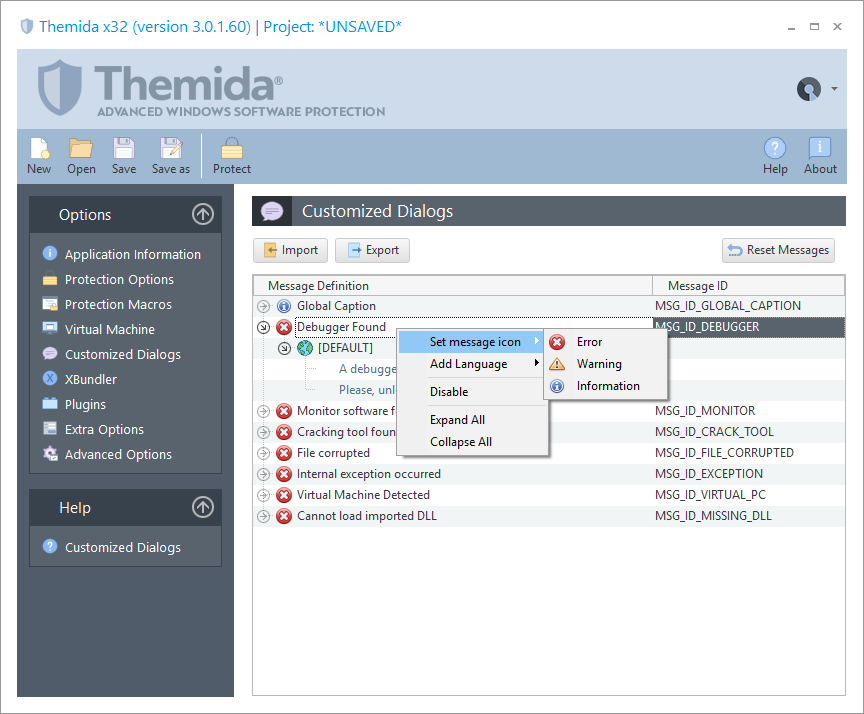

Custom Dialog
For each possible bulletin, you can modify the dialog text and the icon that will be shown with the message.
-
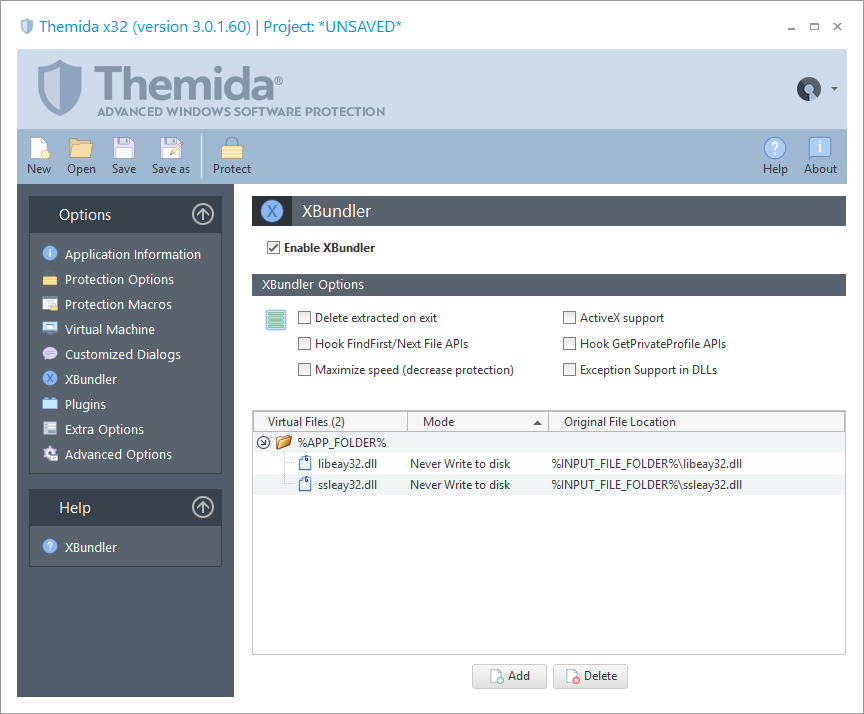

XBundler
XBundler allows you to embed DLLs and data files inside a protected awarding.
-
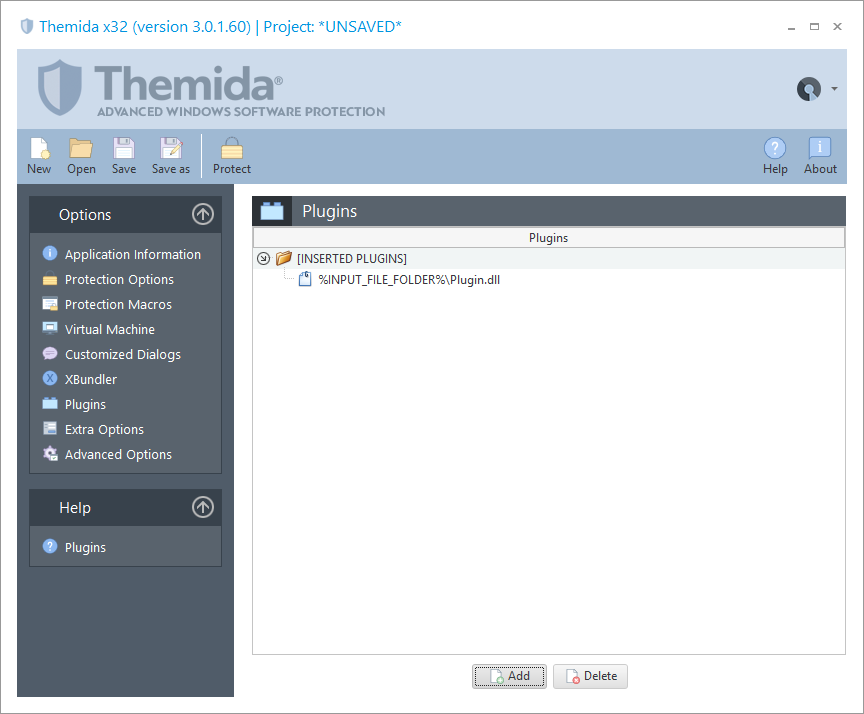

Plugins
Themida allows you to insert custom plugins (DLLs) that volition be embedded inside the protected binary.
-
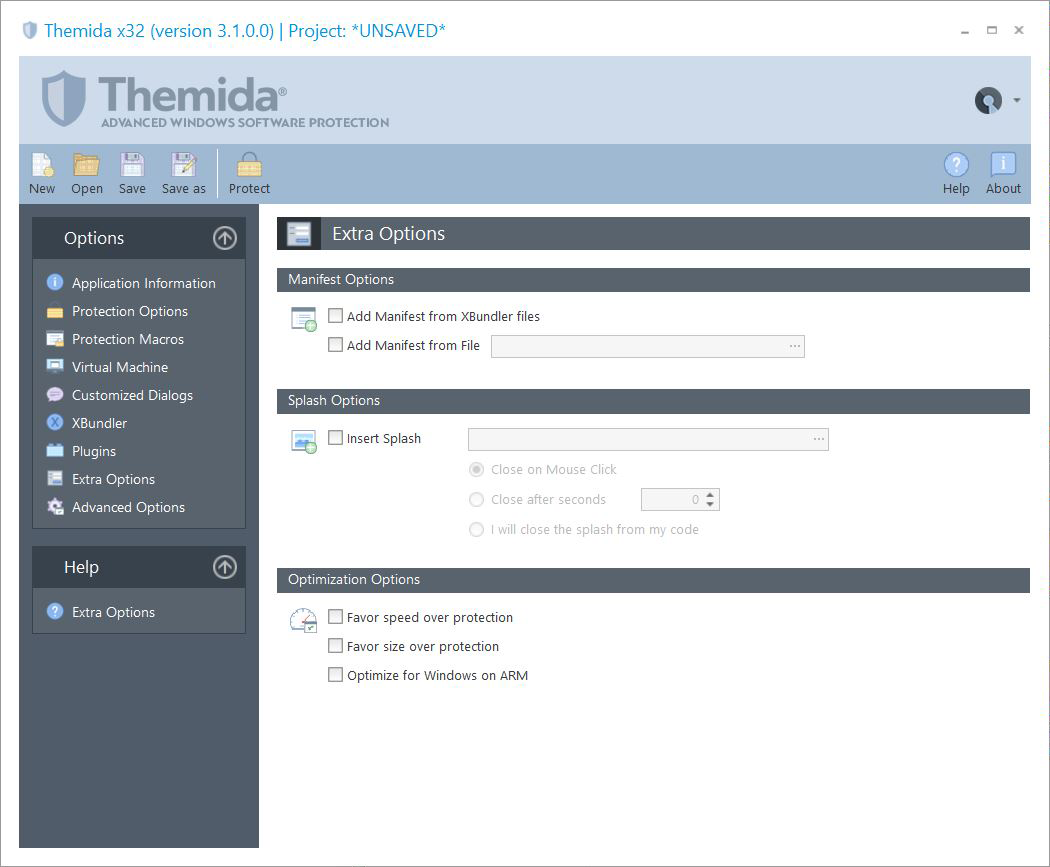

Extra Options
Yous can select the different protection options that you want to include in your application.
-
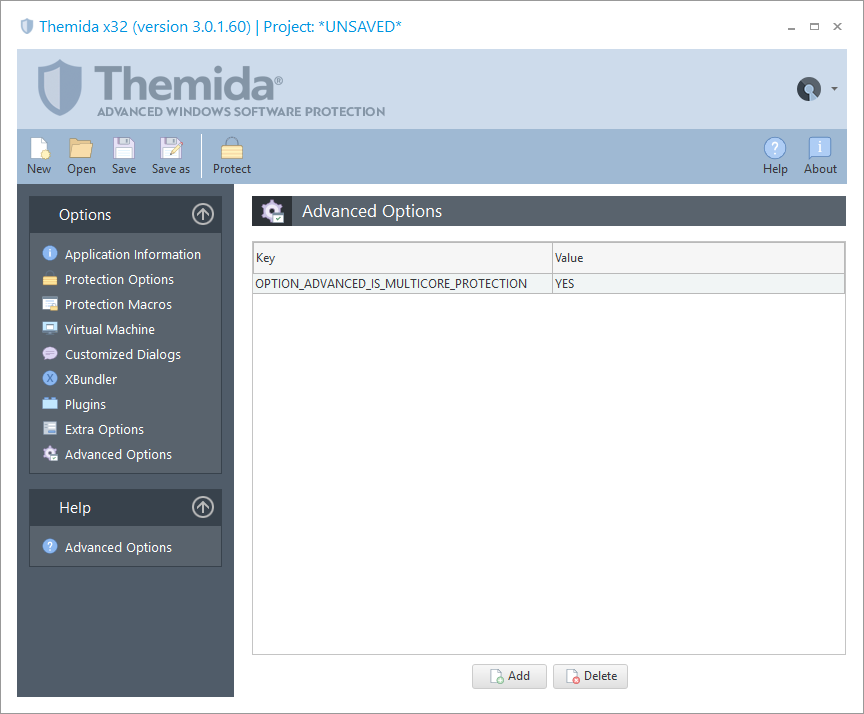

Advanced Options
Options mostly related to compatibility bug with specific applications.
-
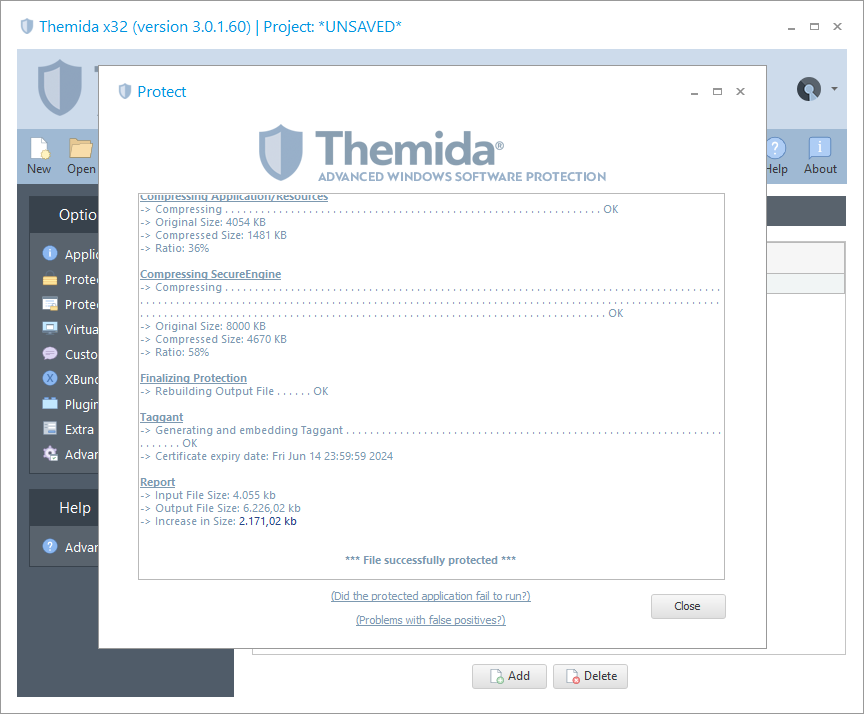

Protection
It shows all the dissimilar steps that are practical when an application is being protected.
Download
Yous can download and evaluate Themida by downloading our DEMO version.
- Demo Release: 3.1.1.0
- Appointment: 27-Apr-2021
Pricing
We offer two types of licenses for Themida, Developer License (199 EUR) and Company License (399 EUR).
If you are a solo programmer, one-homo company or a company with but ane software developer, you simply need to purchase the Developer License.
For companies with more than one software developer, you demand to larn the Visitor License.
You can buy a license for Themida
here.
Other products
WinLicense
Combines the power of software protection (as Themida), with the power of advanced license control. Information technology offers a wide range of powerful and flexible techniques that allow developers to deeply distribute trial versions of their applications.
More
Code Virtualizer
Powerful lawmaking obfuscation system for Windows applications that helps developers to protect their sensitive code areas against Reverse Engineering science with very potent obfuscation code, based on code virtualization.
More

